
Block misbehaving IP addresses using Fail2Ban and AbuseIPDB
When you operate servers, whether physical or virtual, at some point in time you may find yourself victim to bots or botnets trying to access your server over SSH. Even if you configure your server to not expose SSH on port 22 (the default), chances are you will be a target at some point. This is especially true if your server is hosted in a public cloud, since these typically reserve ranges or blocks of IP addresses. Apart from making it as hard as possible to scan your server, you can also serve the community and report those attacks.
What is Fail2Ban?
Fail2Ban is an open-source intrusion detection software package. It scans log files - like /var/log/auth.log - and blocks IP addresses that fail login too many times. It blocks those systems by updating the system firewall, rejecting new connections from those IP addresses. This is not an eternal ban - you can configure how long the ban will stay.
Apart from login attempts using SSH, you can also use Fail2Ban for detecting authentication failures on web pages, or mail servers, or anything that writes a log file. The remainder of this blog focusses on SSH login failures.
What is AbuseIPDB?
AbuseIPDB is a website where webmasters and system administrators can share information about IP addresses that abuse their resources. If you detect someone who attacks your server, you can share their IP addresses including a short comment on the sort of attack. When some machine scans the internet and repeatedly misbehaves by randomly logging in, or even flooding servers with login requests, this builds up a track record. That record can help others decide whether an incoming IP connection might be totally untrustworthy, or maybe should receive the benefit of the doubt.
I used to report attacks manually, but in the last two months or so, I have seen more than 1300 failed attempts on three virtual servers. Most of them originate from IP addresses in various public clouds. Since I am the only one who has SSH access, I can be positively sure that none of them is legitimate. But manually uploading a report each time is simply not worth my time…
Automation time!
Luckily, starting with v0.10.0 (more than three years old at the time of writing) of Fail2Ban, it supports AbuseIPDB. This means I can automatically send a report about this misbehaving IP address.
Unfortunately, the version of Fail2Ban my Ubuntu machines are built against the “old” API of AbuseIPDB. Newer versions of Fail2Ban already include the “new” API. But upgrading to the “new” API isn’t that hard - I needed two change two configuration files for that.
First, I need to edit /etc/fail2ban/action.d/abuseipdb.conf:
# Wrong
# actionban = curl --fail --ciphers ecdhe_ecdsa_aes_256_sha --data 'key=<abuseipdb_apikey>' --data-urlencode 'comment=<matches>' --data 'ip=<ip>' --data 'category=<abuseipdb_category>' "https://www.abuseipdb.com/report/json"
# Correct
actionban = curl --fail --ciphers ecdhe_ecdsa_aes_256_sha -H "Accept: application/json" -H "Key: <abuseipdb_apikey>" --data-urlencode "comment=<matches>" --data-urlencode "ip=<ip>" --data "categories=<abuseipdb_category>" "https://api.abuseipdb.com/api/v2/report"
While I’m there, I went to the AbuseIPDB website > User Account > API and registered an API key. I then copied the API key in the last line of this file.
abuseipdb_apikey = ...
Finally, I needed to edit /etc/fail2ban/jail.d/defaults-debian.conf to indicate that I want to sent the reports to AbuseIPDB:
[sshd]
enabled = true
# Ban IP and report to AbuseIPDB for Brute-Forcing against SSH
action = %(action_)s
%(action_abuseipdb)s[abuseipdb_category="18,22"]
The AbuseIPDB website has a full list of allowed categories.
To verify it’s working, I go to the list of reports I sent:
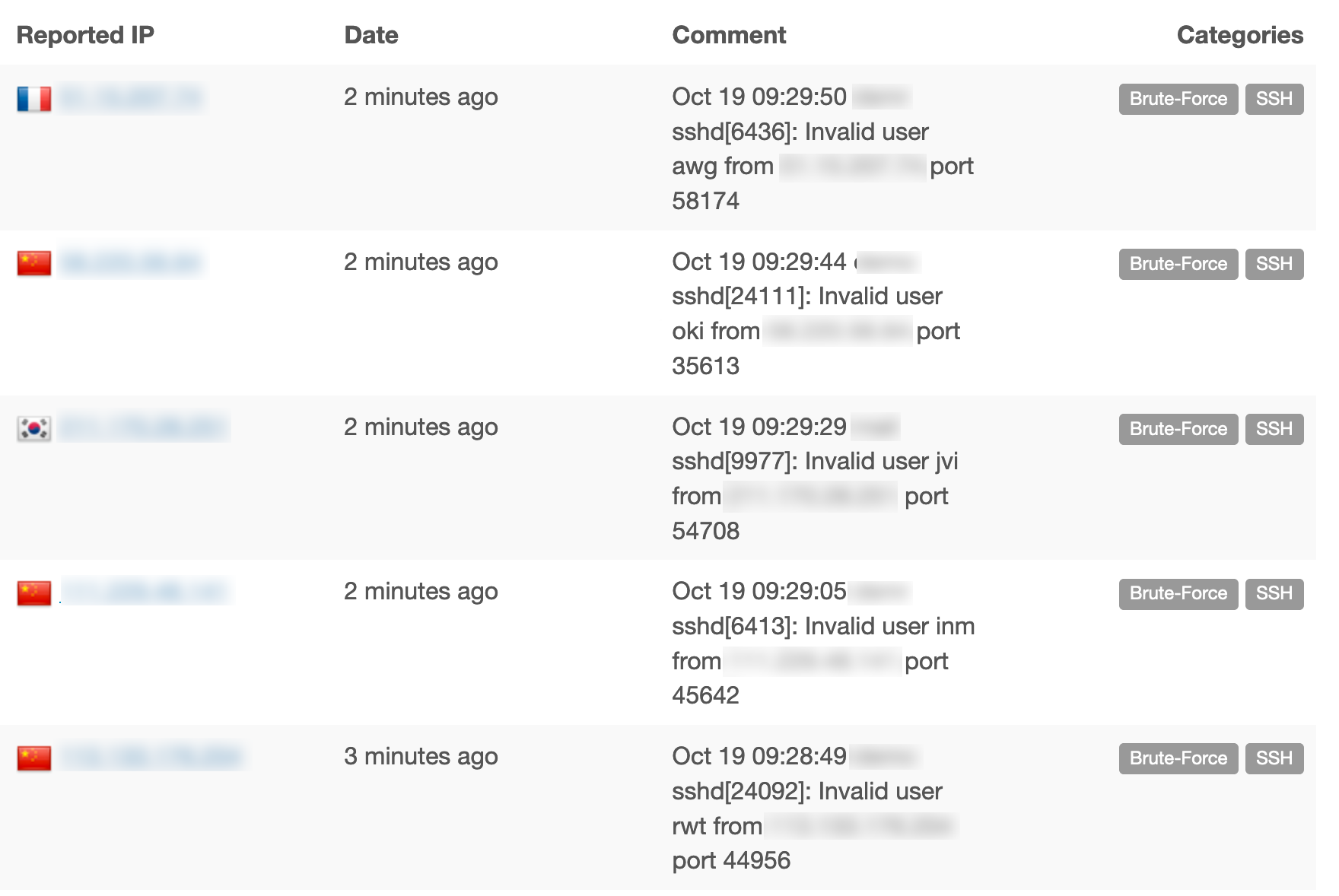
Since I enabled this integration, I have submitted quite a few reports already: